APEX Accelerators (formerly known as Procurement Technical Assistance Centers or PTACs) play a supportive role in helping businesses especially small and medium-sized enterprises navigate the requirements of the Department of Defense's Cybersecurity Maturity Model Certification (CMMC).
While they are not certifying bodies or technical implementation specialists, their responsibilities in aiding clients with CMMC compliance typically include the following:
1. Education and Awareness
Hosting workshops, webinars, and one-on-one sessions to introduce clients to CMMC requirements.
Explaining the different CMMC levels and what each requires from a cybersecurity perspective.
Helping clients understand where CMMC fits into DoD contracting requirements.
2. Pre-Assessment Guidance
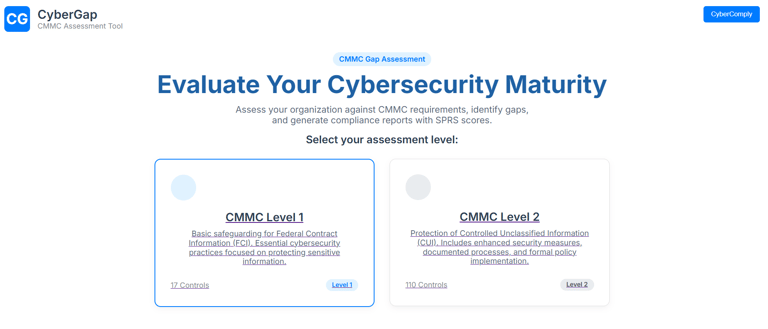
Assisting companies in determining their appropriate CMMC level based on their contract type and data handling (e.g., FCI vs. CUI).
Step-by-Step Process
Review Contract Requirements
Check solicitation, RFP, or existing DoD contract clauses.
Look for indicators like:
DFARS 252.204-7012 (usually means CUI is involved → Level 2)
FAR 52.204-21 only (likely means just FCI → Level 1)
Determine the Data Type Handled
Federal Contract Information (FCI):
Not intended for public release
Basic administrative data
👉 Requires CMMC Level 1
Controlled Unclassified Information (CUI):
Technical, export-controlled, or mission-related info
Protected under NIST 800-171
👉 Requires CMMC Level 2
Interview Key Stakeholders
Ask questions like:
Do you process, store, or transmit technical drawings, ITAR data, cybersecurity plans, etc.?
Are you a prime or sub on a contract requiring NIST 800-171 compliance?
Review Current Practices
Analyze IT systems, subcontractor flows, and document types.
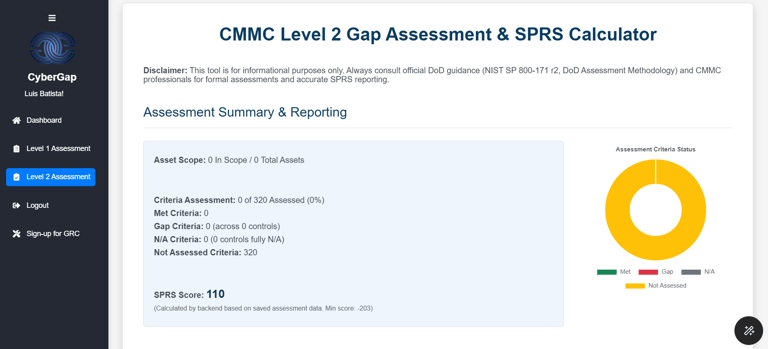
Evaluate whether they have System Security Plans (SSPs) or POA&Ms in place.
Document Recommendation
Provide a written recommendation stating:
Contract(s) analyzed
Data types identified (FCI/CUI)
Recommended CMMC level
Suggested next steps (e.g., gap assessment, remediation)
Example Summary for Client
Based on your current subcontract under Contract XYZ with DFARS 252.204-7012, and your handling of engineering specifications and technical manuals, you are required to protect CUI. Therefore, CMMC Level 2 is the appropriate certification target.
Offering checklists or readiness tools to identify cybersecurity gaps relative to the desired CMMC level.
Referring businesses to self-assessment resources or maturity model documentation.
3. Strategic Planning Support
Helping companies develop an action plan to meet CMMC requirements in a cost-effective and phased manner.
Advising on timelines and budgeting for eventual assessment or certification.
Connecting businesses to vetted cybersecurity professionals or Registered Provider Organizations (RPOs) for more advanced support.
4. Navigation of Certification Ecosystem
Helping clients understand the roles of C3PAOs (Certified Third-Party Assessment Organizations), RPOs, and the CMMC Accreditation Body.
Assisting in locating or connecting with C3PAOs and guiding on what to expect during formal assessments.
5. Ongoing Compliance Assistance
Providing general support on maintaining compliance over time.
Offering updates on evolving DoD regulations or CMMC framework modifications.
Limitations:
APEX Accelerators are not cybersecurity implementation experts. They do not perform gap assessments or conduct CMMC audits themselves, nor do they install cybersecurity controls or software. Instead, they act as educators, guides, and connectors within the broader CMMC compliance landscape.
_______________________________________________________________
_____________________________________________________________________
©2023 Armada Cyber Defense LLC (ACD), DBA CyberComply, ALL RIGHTS RESERVED. ACD is a for profit entity, not associated with the Small Business Development Center (SBDC), Apex Accelerators, Florida International University (FIU), the Small Business Administration (SBA), the Department of Defense, (DOD), or any of their stakeholders.